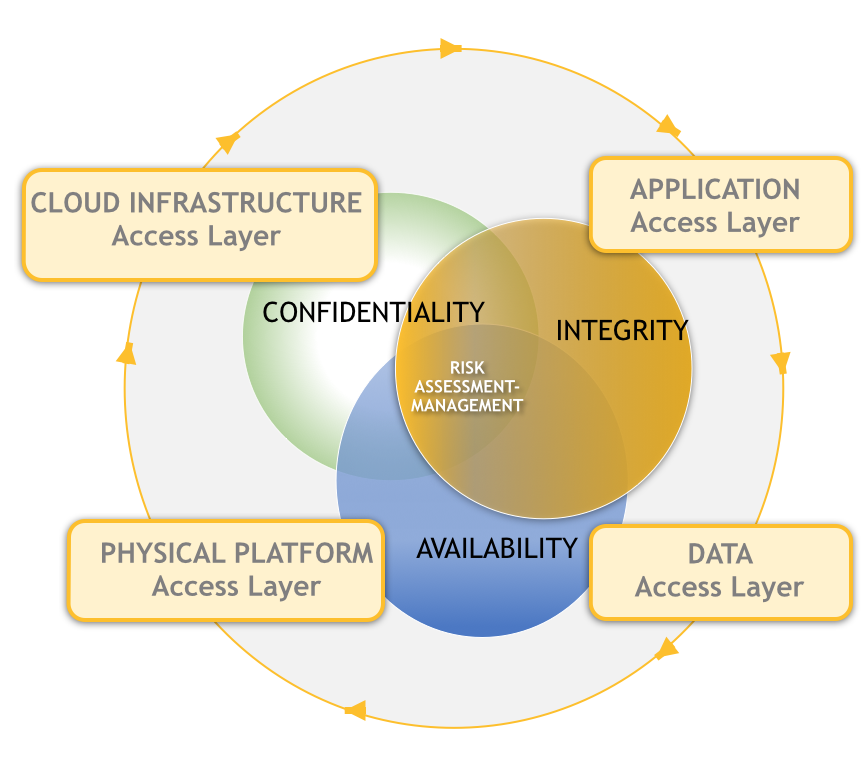
Hardened Cyber Security is a full scope end to end solution our company specializes in. Our team of Cyber Security experts leverage industry best practices such as the Infosec framework to secure and harden your information assets in the cloud as well as on premise. We follow the CIA Triad Blueprint, from the initial assessment, to the recommendations and integration phase. The CIA Triad Framework is defined as follow:
Fundamental Data Security Requirements
1. Confidentiality – A secure system ensures the confidentiality of data. This means that it allows individuals to see only the data which they are supposed to see. Confidentiality has several different aspects:
- Privacy of Communications – How can you ensure the privacy of data communications?
- Secure Storage of Sensitive Data – How can you ensure that data remains private, once it has been collected?
- Authenticated Users – How can you designate the persons and organizations who have the right to see data?
- Granular Access Control – How much data should a particular user see
2. Integrity – A secure system ensures that the data it contains is valid. Data integrity means that data is protected from deletion and corruption, both while it resides within the database, and while it is being transmitted over the network. Integrity has several aspects:
- System and object privileges control access to application tables and system commands, so that only authorized users can change data.
- Referential integrity is the ability to maintain valid relationships between values in the database, according to rules that have been defined.
- A database must be protected against viruses designed to corrupt the data.
- The network traffic must be protected from deletion, corruption, and eavesdropping.
3. Availability – A secure system makes data available to authorized users, without delay. Denial-of-service attacks are attempts to block authorized users’ ability to access and use the system when needed. System availability has a number of aspects:
- Resistance – A secure system must be designed to fend off situations, or deliberate attacks, which might put it out of commission.
- Scalability – System performance must remain adequate regardless of the number of users or processes demanding service.
- Flexibility – Administrators must have adequate means of managing the user population. They might do this by using a directory, for example.
- Ease of Use – The security implementation itself must not diminish the ability of valid users to get their work done.